WCB #8- Screenshot-based malware targets high value organizations in the U.S and Germany.
Weekly Recap
From meddling in elections to dangerous "disguised" Google ads, this week in Cyber had an array of engaging stories. Some of these stories include:
Elections around the world manipulated by hackers - It has been reported that a unit of Israeli-based contractors led by Tal Hannan, has been exposed for interfering in 30 elections globally. It appears they were exposed by undercover reporters which is ironic for a hacker-based group. In my opinion, the reporters did an excellent job here and brought to light novel security concerns of Gmail and Telegram accounts. More on this story can be found here.
Trojan Malware disguised as Google Ads - Google ads can be found on many websites and usually represent a service or product that you may be interested in. Generally speaking, one may click the ad and be redirected to a website where they can purchase said product or service. Unfortunately, Chinese-speaking individuals mainly in China, Taiwan and Hong Kong have become the victims of "disguised" Google Ads where they are redirected to rogue sites that install malware on their devices. More on this story can be found here.
Mental health data on sale? - So much can be said on this topic regarding morality and our right to privacy. Imagine an individual trying to improve themselves regarding their condition only to be bombarded by ads and content that aim to take advantage of their inner demons. Sensitive mental health information should never be on sale and data independence from these data brokers must be obtained. More on this story can be found here.
For this week's main story, I chose to focus on the screenshot-based malware developed by a new threat actor called "866". This group has been targeting organizations in Germany and the United States to steal sensitive data such as SSNs. With a treasure trove of information at their disposal, this threat actor can have a fine payday. With this in mind, these actions by the threat actor seem to be financially motivated.
Summary of Attack
The method of attack can be summarized in these steps:
Threat actor creates Phishing email that contains malicious attachments and links such as the Microsoft Publisher(.pub)
Threat actor sends a Phishing email
The victim clicks a link in the email
An MSI package is downloaded and run.
According to Proofpoint, "It executes an embedded VBS script (WasabiSeed) as well as establishes persistence by creating an autorun shortcut in the Windows Startup folder".
The Wasabi Seed downloads and executes a 2nd MSI file containing "Screenshotter"
"Screenshotter" malware is downloaded and executed on the user's device
Screenshots are then taken and sent to the threat actor's server
Threat actor investigates the data
If not satisfied, the threat actor deploys custom payloads such as "AHK Bot loader" that loads an info stealer named "Rhadamanthys". The info stolen here can vary and include data such as VPN configurations.
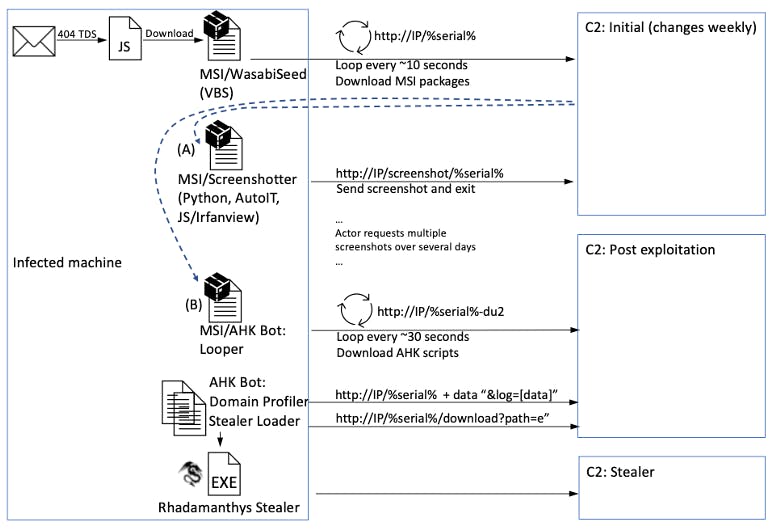
Screenshot showing overall attack chain, Courtesy of Proofpoint
Why I found this story interesting
It's not every day you see "screenshotter-esque" malware. In fact, according to Proofpoint, this type of activity was found in 2019 although the TA866 group was only recently found. I am intrigued by this story because now the threat actor has a database of images from high value-targets which they can go through and determine their next plan of attack. Beyond this, they could even sell this type of information to other hacker groups or create somewhat of a service where they provide similar information to other hackers monthly.
Possible Implications
Loss of revenue
Loss of trust
Sensitive Data Exposure
Possible Solutions
Heightened security awareness & training
Implementing quality Endpoint Detection and Response Technologies
Implement high-quality firewalls
Conclusion
Threat actor, TA866, has announced itself to the cyber world with a simple yet effective method of attack. By focusing on high-value targets in the United States and Germany, the threat actor has narrowed its pool to wealthy victims. Not only does this make their process of screening wealthy victims more efficient, but it also limits the exposure of their TTPs(Techniques Tactics & Procedures) so that their method of attack would remain effective. The threat actor is still active. Proofpoint did an excellent job tracking their activity and reporting its findings on the group.
Resources
08, F., & F, A. (2023, February 8). Screentime: Sometimes it feels like somebody's Watching me: Proofpoint us. Proofpoint. Retrieved February 19, 2023, from https://www.proofpoint.com/us/blog/threat-insight/screentime-sometimes-it-feels-like-somebodys-watching-me
Toulas, B. (2023, February 9). Hacker develops new 'screenshotter' malware to find high-value targets. BleepingComputer. Retrieved February 19, 2023, from https://www.bleepingcomputer.com/news/security/hacker-develops-new-screenshotter-malware-to-find-high-value-targets/
NBCUniversal News Group. (2023, February 13). A researcher tried to buy mental health data. it was surprisingly easy. NBCNews.com. Retrieved February 19, 2023, from https://www.nbcnews.com/tech/security/researcher-tried-buy-mental-health-data-was-surprisingly-easy-rcna70071
Guardian News and Media. (2023, February 15). Revealed: The Hacking and disinformation team meddling in elections. The Guardian. Retrieved February 19, 2023, from https://www.theguardian.com/world/2023/feb/15/revealed-disinformation-team-jorge-claim-meddling-elections-tal-hanan
Hackers using google ads to spread Fatalrat malware disguised as popular apps. The Hacker News. (2023, February 18). Retrieved February 19, 2023, from https://thehackernews.com/2023/02/hackers-using-google-ads-to-spread.html
