Weekly Recap
Top Android phones from China are packed with spyware, research finds: This story by Thomas Claburn highlights the fact that top android phones from China such as OnePlus and Xiaomi are packed with dangerous preinstalled apps. These apps can transfer sensitive information without the consent of the individual. More on this story can be found here.
Researcher breaches Toyota supplier portal with info on 14,000 partners: The security researcher codenamed "EatonWorks" recently discovered a backdoor in Toyota's system. Through this backdoor, a malicious individual could access an existing user account once the individual knew their email. More on "EatonWorks" discovery can be found here and here.
Truth finder, instant checkmate confirms data breach affecting 20 million users: This article by Lawrence Abrams details a breach that PeopleConnect stated they recently discovered. PeopleConnect is the owner of TruthFinder and Instant Checkmate which are both background services. The actual attack involved hackers leaking a 2019 database that contained customer information. More on this story can be found here.
For this week's main story, I chose to focus on the threat actor known as "NewsPenguin".
Background
"NewsPenguin" attacked PIMEC(Pakistan International Maritime Expo and Conference) which was an event held by the Pakistan Navy and organized by the Ministry of Maritime Affairs.
The title "NewsPenguin" was given to the threat actor by the BlackBerry research group for two specific reasons. A unique XOR key and the content-disposition header name parameter being set to "getlatestnews". XOR stands for "Exclusive or" and it is a logical operation in which true arguments differ(one is true and the other is false). The content-disposition header indicates what content will be displayed inline in the browser. The threat actor is relatively new with no prior history of attacks.
Summary of Attack
From the report shown, the threat actor is targeting Pakistani entities that are government-based or conduct important business with the Pakistan government. An example of such a company would be a weapons manufacturer such as the Pakistan Ordnance Factories. Due to the concentrated nature of the targets and the attack being designed for these marine-based targets, the BlackBerry research group suspects the attacker is a nation-state or hackers for hire working for a nation-state threat actor.
Below are some of the main methods of attack used by "NewsPenguin":
Phishing: The threat actor used spear-phishing to target individuals with a weaponized document named "exhibitor manual". Spear-phishing is similar to phishing where malicious emails are sent to individuals. The difference between the two is, spear-phishing is used to target a specific individual or group. In this case, the threat actor was targeting Pakistani-related entities
Image showing "Exhibitor Manual" document
Remote Template Injection: Through the "exhibitor manual", the threat actor can deploy a malicious payload through the use of remote template injection. According to Mitre, template injection is the method by which adversaries create or modify references in user document templates to conceal malicious code or force authentication attempts. The threat actor was taking special precautions to remain hidden while carrying out this attack.
Espionage Tool: The threat actor uses a Windows executable called updates.exe which is a spy tool with the capability of bypassing sandboxes and virtual machines.
XOR Encryption: Contents of Binary are encrypted with XOR encryption where "penguin" is the encryption key used. XOR encryption is robust in that, if one does not know the XOR encryption key before the decryption process, then their chances of decrypting the data are zero. More on this can be found here.
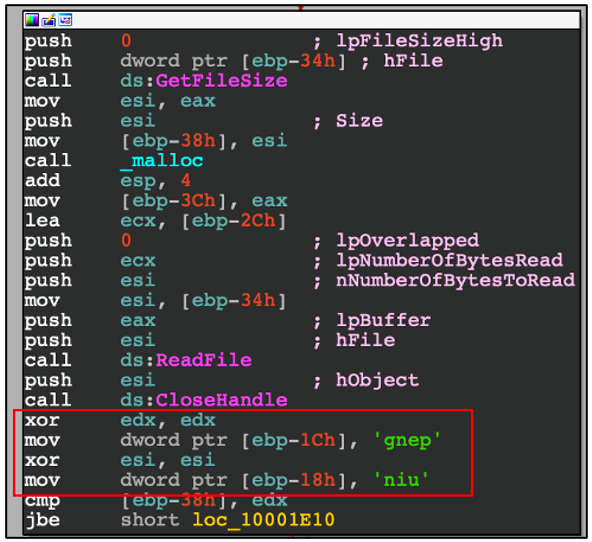
Image from BlackBerry highlights XOR encryption
More detail on this attack can be seen here.
Why I found this story interesting
This threat actor seems to be entirely focused on government organizations. Compared to other events concerning phishing campaigns, the motivations of the hacker and the victim pool are unclear. In my opinion, the individual or team initiating this attack has to be backed by a foreign entity or is a former employee of some kind seeking retribution. An insane amount of risk for little to no financial reward gives credence to my opinion.
Possible Implications
Loss of revenue
Loss of trust
Sensitive Data Exposure
Solutions
Implement antivirus software
Monitor network traffic and processes to prevent future attacks
Network intrusion prevention
Frequently update and patch systems
Heightened security awareness & training
Conclusion
The research & intelligence team at BlackBerry did a phenomenal job with reporting the entire execution chain of "NewsPenguin". This attack on Pakistan-based organizations was reminiscent of textbook phishing attacks that contain a weaponized attachment or link. From the use of a social engineering tactic to the use of malware in the form of a payload, the attack on the surface seemed simple. Diving deeper, however, the motivations of this attack and the preparation of this attack allude to the threat actor being backed by a government entity.
Resources
Claburn, T. (2023, February 7). Android phones from Chinese vendors share private data. The Register® - Biting the hand that feeds IT. Retrieved February 12, 2023, from https://www.theregister.com/2023/02/07/chinese_android_phones_leak_pii/
Toulas, B. (2023, February 7). Researcher breaches Toyota Supplier Portal with Info on 14,000 partners. BleepingComputer. Retrieved February 12, 2023, from https://www.bleepingcomputer.com/news/security/researcher-breaches-toyota-supplier-portal-with-info-on-14-000-partners/
NewsPenguin threat actor emerges with malicious campaign targeting Pakistani entities. The Hacker News. (2023, February 10). Retrieved February 12, 2023, from https://thehackernews.com/2023/02/newspenguin-threat-actor-emerges-with.html
Abrams, L. (2023, February 4). TruthFinder, instant checkmate confirm data breach affecting 20m customers. BleepingComputer. Retrieved February 12, 2023, from https://www.bleepingcomputer.com/news/security/truthfinder-instant-checkmate-confirm-data-breach-affecting-20m-customers/
NewsPenguin, a previously unknown threat actor, targets Pakistan with ... (n.d.). Retrieved February 12, 2023, from https://blogs.blackberry.com/en/2023/02/newspenguin-a-previously-unknown-threat-actor-targets-pakistan-with-advanced-espionage-tool
Template injection. Template Injection, Technique T1221 - Enterprise | MITRE ATT&CK®. (n.d.). Retrieved February 12, 2023, from https://attack.mitre.org/techniques/T1221/
