Weekly Recap
This week in cyber felt a bit dystopian if you ask me. Stories ranged from individuals being scanned with facial recognition to enter a stadium to security cameras not being as "secure" as they were marketed to be. Below is a list of events that I found interesting in the past week:
FDIC was found to not test the cyberdefenses of banks effectively. The FDIC's Office of Inspector General found major flaws in the agency's overall cyber defense set up. It was found that staff lacked frequent security and awareness training and the procedures surrounding data transfer and storage were outdated.
More on this story can be found here.Anker Eufy security cameras were not as secure as marketed. It was revealed late last year by The Verge that Anker's allegedly always-encrypted Eufy cameras were producing unencrypted streams. This revelation came about after The Verge was able to access a video stream from a Eufy camera, from another part of the country with zero encryption.
More on this story by Sean Hollister can be found here.
Facial recognition is being used at Madison Square Garden: Madison Square Garden corporation is using facial recognition to identify and prevent lawyers that represent clients who have ongoing cases against the owners of the organization. Letita James is an example of one such lawyer that is banned from the venue and is seeking retribution against the organization.
More on this can be found here.
Despite these interesting events, for this week, I chose to focus on the crafty packer known as TrickGate. TrickGate has been used by multiple malware families such as HawkEye and Trickbot.
Background of TrickGate
Dubbed a "master of disguise", TrickGate is a shellcode-based packer that can assist in concealing payloads behind a layer of wrapper code. TrickGate, in particular, has undergone frequent changes which have allowed the packer to go unnoticed. Before we go any further, I think we should go over some definitions.
Packers: Packers are known for circumventing detection using a variety of methods such as appearing as harmless files. It is a form of code obfuscation and is also known as executable compression since it makes files smaller to hinder reverse engineering.
More on this definition can be found here.
Payloads: According to TechTarget, a payload is the carrying capacity of a packet or other transmission data unit. In this case, malware payloads were used. A malware payload contains malicious code used to exploit or harm IT systems. Any type of malware can be integrated into the payload and these payloads can be distributed by worms or phishing emails.
More on this definition can be found here.
Shellcode: Part of the payload, shellcode is a set of instructions used to run a command that can compromise an IT system. Threat actors use it to introduce malware such as trojans to obtain sensitive data.
More on this definition can be found here.
TrickGate has been offered as a service (Malware as a service) to threat actors since 2016. It is primarily used in the manufacturing sector but has impacted other industries such as the healthcare industry.
Summary of Attack
Phishing emails & Malicious links are common methods used so that TrickGate can gain entry into a system. By clicking on malicious links, a shellcode loader can be downloaded. This shellcode loader decrypts and launches the actual payload into memory.
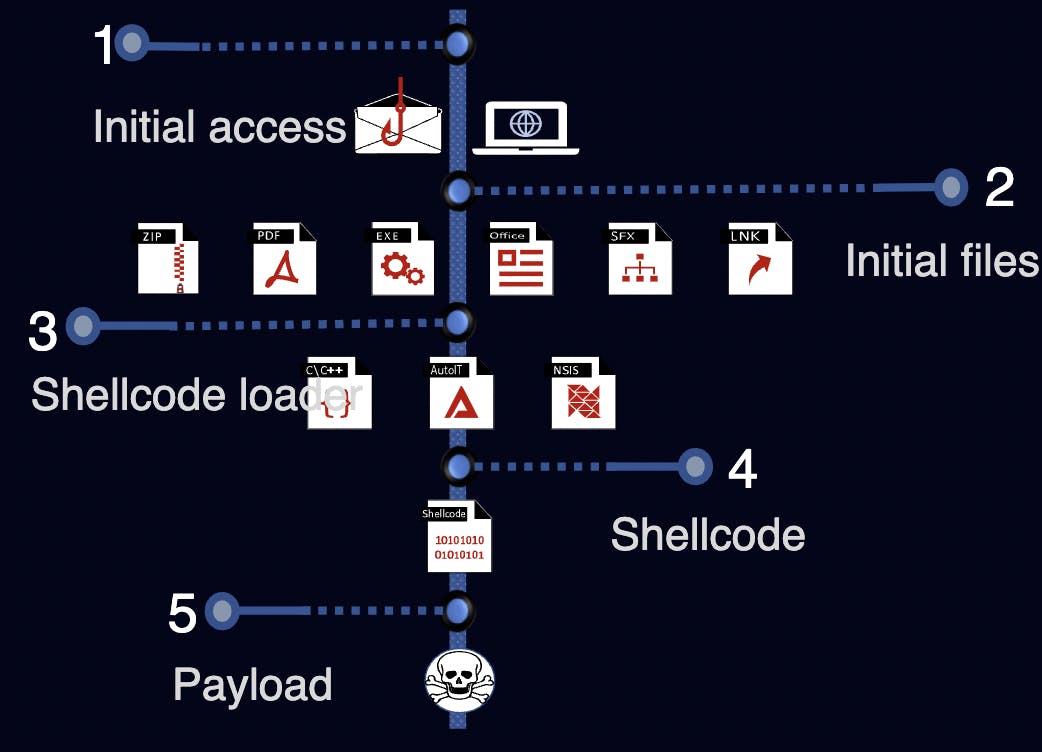
Diagram showing the attack flow of TrickGate by Check Point Research
From the diagram above, TrickGate usually gains initial access to a system via phishing emails.
The initial files that are introduced come in the form of archived executables carrying the shellcode.
The shellcode loader then decrypts and runs the shellcode
The shellcode then decrypts the payload and injects the malicious code into the system.
The payload can be one of many malware types from trojan horses to ransomware.
A detailed report of TrickGate can be found here.
Why I found this story interesting
To go unnoticed for a small period of time is one thing, but to be unnoticed for six years is fascinating. No identifiers and no signatures were found to determine the existence of this packer. This leaves one to ponder on the involvement that TrickGate may have had in the damage that threat actors have caused over these years. With this in mind, TrickGate is indeed worthy of the title "master of disguises".
Possible Implications
Loss of revenue
Loss of trust
Sensitive Data Exposure
Solutions
Implement antivirus software
Implement the latest software updates.
Frequently update and patch systems.
Heightened security awareness & training
Conclusion
With this revelation, this information regarding TrickGate can be used to help in identifying malware. If the packer is blocked, the payload has little to no chance of compromising IT systems. Arie Olshtein did an amazing job reporting this alarming discovery.
Resources
Researchers uncover Packer used by several malware to evade detection for 6 years. The Hacker News. (2023, January 31). Retrieved February 5, 2023, from https://thehackernews.com/2023/01/researchers-uncover-packer-that-helped.html
Ivanova, I. (2023, January 27). Madison Square Garden uses face recognition to keep out enemy lawyers. that may be illegal. CBS News. Retrieved February 5, 2023, from https://www.cbsnews.com/news/madison-square-garden-face-recognition-illegal-new-york-attorney-general-letitia-james/
Hollister, S. (2023, January 31). Anker finally comes clean about its EUFY security cameras. The Verge. Retrieved February 5, 2023, from https://www.theverge.com/23573362/anker-eufy-security-camera-answers-encryption
Jones, J. H. (2023, February 1). Watchdog warns FDIC fails to test banks' cyberdefenses effectively. FedScoop. Retrieved February 5, 2023, from https://fedscoop.com/watchdog-warning-fdic-cybersecurity/
Froehlich, A., & Loshin, P. (2021, October 25). What is a payload? Security. Retrieved February 5, 2023, from https://www.techtarget.com/searchsecurity/definition/payload
Arntz, P., & ABOUT THE AUTHOR Pieter Arntz . (n.d.). Explained: Packer, Crypter, and protector: Malwarebytes labs. Malwarebytes. Retrieved February 5, 2023, from https://www.malwarebytes.com/blog/news/2017/03/explained-packer-crypter-and-protector
Etal. (2023, January 31). Following the scent of TrickGate: 6-year-old Packer used to deploy the most wanted malware. Check Point Research. Retrieved February 5, 2023, from https://research.checkpoint.com/2023/following-the-scent-of-trickgate-6-year-old-packer-used-to-deploy-the-most-wanted-malware/
