Weekly Recap
This week in cybersecurity felt less eventful as compared to last week but still had some interesting events. Some of these events include:
Slack's private GitHub repositories were stolen, but thankfully, customer data was not compromised.
Peter Zatko, also known as Mudge, joined the cybersecurity firm Rapid7. Peter Zatko is one of the pioneers of information security in the U.S. belonging to the group L0pht. This move, in my opinion, definitely improves the already solid public image of Rapid7.
Irish privacy watchdog fined Meta 400 million due to Meta failing to inform users of that region on how their data was being used
For this week's story, I chose to focus on the event concerning an ex-General Electric engineer exfiltrating data into China. Xiaoqing Zheng was an employee at the company specializing in turbine sealing technology. Zheng was a trusted employee and worked at the company from 2008 to 2018. For the benefit of the Chinese government, however, Xiaoqing together with some of his family members conspired to steal proprietary information associated with General Electric's ground and aviation-based turbine technologies. One interesting fact of this action is China recently laid out a 2030 plan where this area of turbine technologies would be a top priority for them to improve upon. That plan can be found here. Along with this, Xiaoqing was a major owner of two Chinese companies that also were involved in turbine technology. He informed his employer of this and miraculously was still allowed to work and conduct business at the company. As time passed, General Electric would later regret this decision as they found out that the proprietary information was being transferred to these companies.

Xiaoqing Zheng at James T. Foley Federal Courthouse on January 3rd, 2023.
Summary of Attack
Insider threat methods of attacks can vary depending on their goals, the size of the company and skill level. In this case, Xiaoqing was patient in his approach and decided to use steganography as one of his main methods of attack.
Steganography involves using procedures or techniques to hide sensitive data in common data to bypass detection. Some common examples of this technique are embedding text in a painting or hiding an image in a video where the image is only visible if played at a certain frame rate.
Xiaoping used an advanced file encryption software called AxCrypt. AxCrypt allowed Xioaqing to save a large number of encrypted files on his work computer which he could move around without the G.E's information security team knowing what was in the files. Thankfully, the SOC(Security Operations Center) at General Electric was on top of things and monitored this activity for over a year waiting to see what would become of these encrypted files. Xiaoqing then moved them to a temporary folder and then hid those files in the code of another file which was a digital photograph of a sunset. Textbook steganography in my humble opinion.
Below are some screenshots from the official court document that showcase the method of attack used
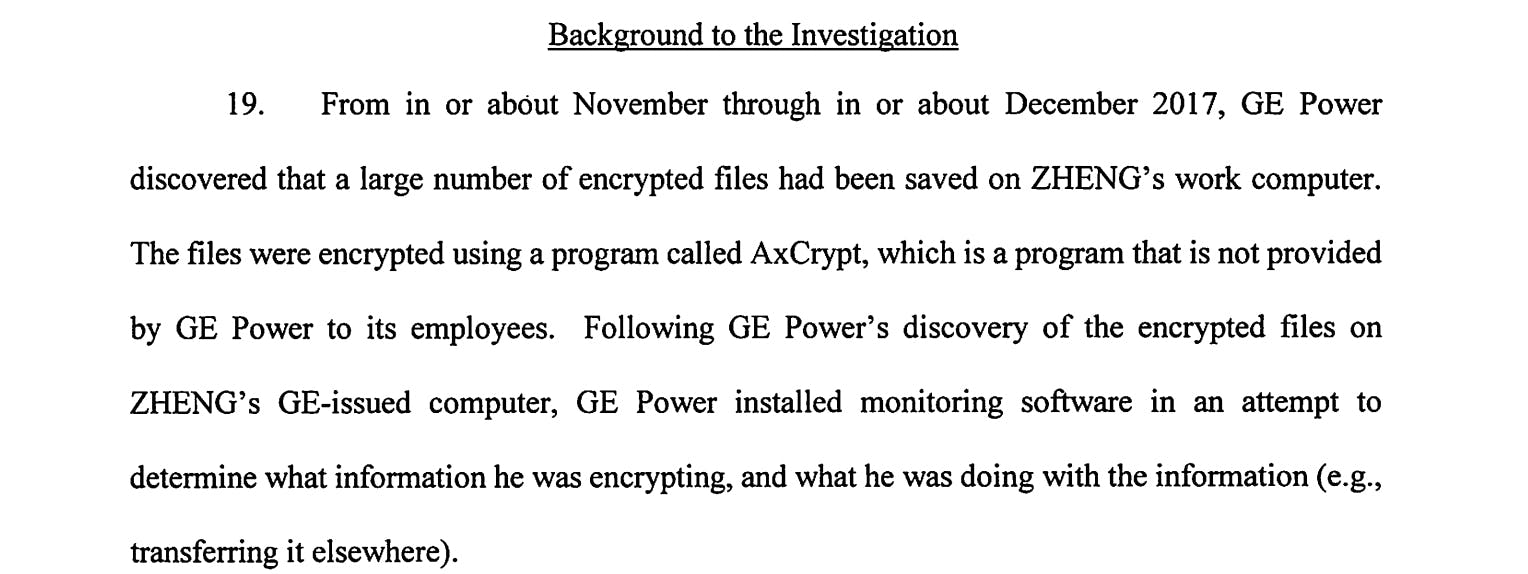


Here is the link to the PDF of the official court documents.
Why I found this story interesting
Insider threats are always interesting to me. Reading about these events evokes feelings of mystery, wonder and excitement. These news stories are gentle reminders that nations or entities are constantly engaging in different forms of warfare. The type of obstacles one has to face to exfiltrate the information, the insanely high risk associated with this task and the amount of preparation and time that goes into executing these attacks has always fascinated me. For me, it is something that I can never do, but it is interesting to read.
Possible Implications
Loss of trust between employer and employees associated with foreign countries
Reputational damage to General Electric.
Possible Solutions
Content Threat Removal (CTR) - This data security solution protects data from unnoticeable threats. It is essential in the fight against individuals using steganography. More on this solution can be found here.
A more thorough vetting process
Avoiding conflicts of interest
Antivirus software for common signatures used by hackers
Conclusion
Looking at the situation as a whole and analyzing the verdict given, I am a bit confused as to how a million-dollar data exfiltration warrants only a two-year sentence behind bars, a 7,500 fine and a one-year post-imprisonment supervised release. Nevertheless, when I compared it to other insider threat events, such as a former U.S Army contractor being sentenced in 2019 to the same amount of time for causing over 1 million in damages to the Pentagon, it appears this is somewhat a standard for the punishment given for this activity (of course it can vary). In the end, justice was served and the information security team did a good job monitoring the individual.
Resources
Hardcastle, J. L. (2023, January 4). Ex-GE engineer sentenced for stealing turbine tech for China. The Register® - Biting the hand that feeds IT. Retrieved January 7, 2023, from https://www.theregister.com/2023/01/04/ge_turbine_china_prison/
Regmedia.co.uk. (n.d.). Retrieved January 8, 2023, from https://regmedia.co.uk/2023/01/04/xiaoqing_zheng_indictment_ge_trade_secrets.pdf
Gavin, R. (2023, January 4). Ex-GE engineer gets 2 years in federal prison in espionage case. Times Union. Retrieved January 8, 2023, from https://www.timesunion.com/news/article/Former-GE-engineer-gets-two-year-prison-term-in-17691033.php#photo-23328289
Globally rewarded and easy to use file encryption. AxCrypt. (n.d.). Retrieved January 8, 2023, from https://axcrypt.net/
Venkat, A., & Ross, R. (n.d.). Former Army contractor gets prison term for insider attack. Bank Information Security. Retrieved January 8, 2023, from https://www.bankinfosecurity.com/former-army-contractor-gets-prison-term-for-insider-attack-a-13160?utm_campaign=meetedgar
